In recent years, firms that want to save time, be more flexible, save money, and increase productivity have turned to outsourcing. About 43 percent of companies in the United States outsource programming jobs. Outsourcing permits these firms to focus on what they do best while contracting the services of other firms. However, it is fraught with risks. Threats to the security of their intellectual property rights are among them. In this article we will demonstrate how to protect intellectual property when outsourcing.
What are intellectual property rights?
Intellectual property rights cover the legal protection of unique products, inventions, industrial designs, creative works, trade secrets, and other items or services generated by the human intellect. The intellectual property rights of a firm are equally or more valuable than the physical assets of the firm. The rights entitle its authors to utilize them for a specific period of time or in perpetuity.
An outsourcing arrangement may require the firm to share its intellectual property with vendors. Several risks may arise from such arrangements. Therefore, it is important to protect the firm’s intellectual property rights, when entering into outsourcing agreements.
Before discussing how to protect your firm's intellectual property when outsourcing, it is important to understand the types of intellectual property and the nature of risks that arise from them.
Types of intellectual property rights
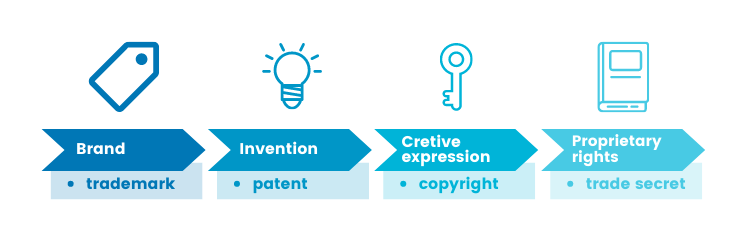
Intellectual property rights include copyrights, patents, trademarks, and trade secrets, all protecting various forms of intellectual capital.
- Copyrights safeguard creative expressions, such as literary, artistic, and musical works. An example of a literary work is a software code. A copyright prevents others from copying your firm’s code without the firm’s permission. Copyrights can also protect the images, texts and videos on your firm’s website, or in sales materials, manuals, customer databases, suppliers’ lists, and other databases. A copyright protection in the U.S. lasts during the lifetime and for 70 years after the lifetime of the author.
- Utility Patents protect new inventions or improvements to existing inventions. These inventions include concepts, features, methods, algorithms, operating system techniques, underlying critical software processes and functionalities. An example of a utility patent is Amazon’s One-Click. A patent protection covers one product or service and lasts for 20 years. It grants you the exclusive right to use, sell or license your software.
- Trademark protection shields trademarks, such as your brand, logo, business name, domain name or slogan from use by others. Trademarks are registered distinctive marks that identify your firm and the services it provides and distinguishes it from others in the market. An example of a trademark is Apple’s bitten apple. A trademark protection is to be renewed every 10 years in the U.S.
- Trade Secrets safeguard technical data, user data, internal processes, research data, patterns, and mechanisms that are not in the public domain. They could also shield parts of the code base, such as mathematical formulas, or models of software. An example of a trade secret is Google’s search algorithm. A trade secret protection safeguards the secrets in perpetuity and gives you competitive advantage in your industry.
- Industrial design rights safeguard the physical designs of objects, including their shapes, configurations, patterns, surfaces, colors, and other visual features. It may also protect graphical and user interfaces of software programs.
Before you begin outsourcing, determine which intellectual property you are ready to release and which should remain within the organization. If any of the job is dependent on something owned by a third party, always verify your agreement with them before providing any sensitive information.
The importance of intellectual property rights
Intellectual property rights are critical for economic development, employment creation, and a higher standard of living. Without the power to create - both culturally and technologically - humanity will be unable to grow. National laws that provide legal protection for innovations further stimulate new creations by explicitly regulating the interests of innovators and the public in a way that fosters creativity and innovation. All of these have a direct effect on our health and quality of life.
While most software products are covered by copyright law, certain features and designs may also be patented. There are a variety of legal procedures and frameworks in place to assist you in securing your intellectual property - the law is on your side, but you must also do your due diligence when it comes to safeguarding your creation. Bear in mind that national legislation safeguarding intellectual property varies by country.
Where do IP related risks originate?
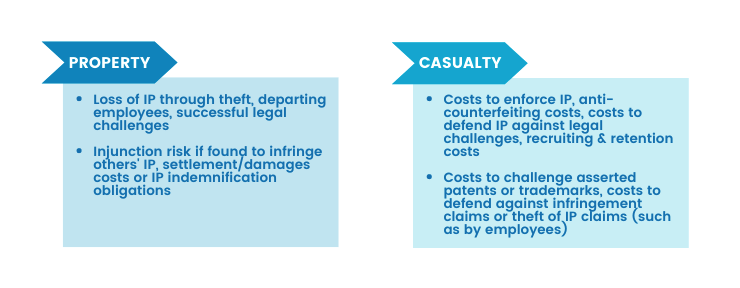
Risk is the chance of something going wrong. IP risks include threats to the disclosure, infringement, or loss of intellectual property rights of a company. The nature of IP risks depends on the type of IP involved and may be categorised into:
- Property risks which are risks arising from loss of intellectual property; and
- Casualty exposures which are risks arising from your firm’s liability for infringement of the IP rights of others:
Companies and organizations face IP related risks from a multitude of sources, namely:
- From within the organization itself. A significant percentage of the IP related risks that an organization faces originate from its own employees. At times, this is owing to employees' lack of awareness, negligence, or lack of education concerning intellectual property. At other times, it is a premeditated act. An example of employees’ lack of awareness is executing agreements on behalf of the company without understanding the intellectual property terms of such agreements or disclosing the company’s trade secrets to a competitor. Employees could also deliberately transfer, misuse, or sell valuable intellectual property of a firm, such as its software code or customer lists.
- From entities in the ecosystem of the organization. IP risks could also arise from collaboration with third parties, such as key suppliers, vendors, organisations, communities, or end-users. Such collaboration may require your firm to share intellectual property with third parties. Some third parties within your business's ecosystem may simply fail to handle your IP with the care and respect it deserves, resulting in IP-related hazards. You should also pay attention to the terms and conditions of such collaborations which may bear some IP risks.
- From competitors. The products and services of every competitor carry a potential IP risk to that of your firm. Competitors are at risk of breaching your patent rights or creating similar graphic user interfaces that infringes your industrial designs. Examples of the IP risks from competitors may be found in the smartphone industry and the several IP lawsuits between Apple and Samsung.
- From independent 3rd parties. IP risks may also arise from independent third parties, such as IP holding companies and related entities. If your firm is a subsidiary or holding company within a group structure or has other related entities, IP-related risks could arise from licensing IP to these entities. Furthermore, these entities could expose the IP to risks by misusing the IP. Patent trolls who hold patents and do not commercialize them, but wait for companies to infringe the rights to these patents and then enforce their rights through litigation, cash settlement, and licensing may also pose risks to the company.
- From illegal entities. The activities of Hackers and counterfeiters may also give rise to IP-related risks. Hackers may gain illegal access to your company’s trade secrets, software code, and computer infrastructure. Counterfeiters may also develop counterfeit products that infringe on your trademark rights, compete with your products in the market, and sink your firm’s profits. According to the Organisation for Economic Co-operation and Development, trade in counterfeit goods stood at 3.3% of world trade as at 2019.
IP risks in software development
Some examples of IP related risks arising in software development are:
- Patent related risks. The first patent related risk with software development is the likelihood of not obtaining a patent registration. Due to patent eligibility guidance in the U.S., it is increasingly difficult to obtain a patent for software solutions. Meanwhile, inventors are all working to solve problems and your invention may not be so different from others, to qualify for patent registration.
- Trade secret related risks. the biggest risk to a trade secret is the risk of it becoming easily accessible. A trade secret loses its commercial value once it becomes public knowledge. This could arise from a founding member leaving the company with some trade secrets to establish a competing business, or a cyber criminal hacking into the company’s network.
- Soft IP related risks. These are IP related risks arising from ‘soft IP’, such as trademarks, copyright, and domain names. One of these risks is the refusal of companies to register their trademarks or domain names (as trademarks) in their country of operation and in countries they plan to enter in the short term. If these brand names are used by other businesses, it becomes difficult to enforce the firm’s IP. Another risk with domain name registration is cyber squatting. To avoid this, you should defensively register similar domain names as yours. For example, samsong.com and samsung.com. There is a risk of a vendor or other third party squatting on similar domain names.
Open source software related risks. These are risks associated with computer software whose source code is available for use with a public license. The copyright holder exercises the right to grant a license to study, change, or distribute the software. One of these risks is copyright infringement. This may occur when a programmer uses an open source software without giving proper credit to the author or violating the licence terms and conditions in any other way.
Bear in mind that open source software only gives you licence to use the code in a specified way, i.e., in accordance with the specific terms and conditions of the licence. It does not confer ownership. Make sure your outsourcing company provides you with a comprehensive inventory of all software packages utilized in the development of your product. They should also provide assurance that they have not infringed on the intellectual property of a third party by incorporating it into your software. Finally, the contract should include an indemnity clause that gives monetary protection for any actions taken against you for illegal use of third-party software.
6 Steps to Protect Your IP When Outsourcing Development
Having understood the nature of IP risks that arise from software development, we will discuss six steps to protect your IP when outsourcing software development.
Do your due diligence
It is important to conduct due diligence on a vendor before entering into an agreement with the vendor. The scope of such due diligence should include the vendor’s reputation and any past breaches of its clients’ intellectual property rights.
You should also investigate the vendor’s internal risk measures, their ability to safeguard your IP and what its response would be to a data breach within their organization. If you are hiring a vendor overseas, you should also consider how your IP will be protected by the laws of that country and the legal remedies available to you for the breach of your IP rights. You may also use freelancing platforms that show reviews and feedback from past clients.
In addition, you should confirm the internal processes of the vendor including whether the job would be subcontracted to a third party and if so, the measures that have been put in place to protect your IP.
You should check the legal representation of the vendor online to ensure you are speaking with the right person and that they are an authorised representative with the power to act on behalf of the organization you deal with.
Finally, you may also visit the vendor’s place of business to confirm the security measures that have been put in place and to build a strong relationship with the vendor. While word of mouth is great, you should not rely entirely on it but conduct your due diligence on the vendor.
Sign Non-Disclosure Agreement (NDA)
Before hiring a vendor, or after hiring a vendor but before sharing any confidential information, you should enter into a non-disclosure agreement (NDA) with the vendor.
As the name implies, NDAs place an obligation on a party or parties not to disclose certain information, including software development or technical data, to third parties. The NDA should be wide enough to cover the scope of the vendor’s services, but also narrow enough to define confidential information and what amounts to a breach. The NDA should also bind the vendor’s employees or subcontractors who would be working on the task.
The non-disclosure obligations in NDAs would typically outlive your business relationship with the vendor. This may be in perpetuity - if possible - or for a number of years after the completion of the project. Therefore, at the end of your project, you should reiterate the vendor’s obligations to not disclose confidential information.
Use the legal framework applicable to IP in your country
The legal framework and available measures to protect intellectual property rights differ from country to country. For example, European Union countries are required to comply with the EU regulations on intellectual property. Meanwhile, companies in the U.S are required to comply with the Constitution and the regulations issued by the U.S. Copyright Office and the U.S. Patent and Trademark Office.
It is important to pay attention to the legal framework of the country within which the vendor operates and to know how your intellectual property rights will be treated. Will your intellectual property rights be recognised by the laws of that country? Will you be able to enforce your rights in the event of breach within such a country? It is advisable to seek legal counsel before executing an outsourcing agreement.
Draft a comprehensive Master Service Agreement
A Master Service Agreement is an agreement that documents the terms of future contracts between the parties. Also known as a Framework Agreement, it states the terms of service delivery, work standards, payment terms, rights and liabilities, confidentiality, ownership of intellectual property rights to the final product, and data protection mechanisms.
It is important to pay attention to ownership of the IP rights to the work product. Vendors would usually prefer to retain ownership to use the deliverables in future projects. The contract should clearly state the creators, authors, and owners of the work product. It should identify your firm as the owner of the work product and preserve your right to use, assign, and modify the work product.
The Master Service Agreement should also include dispute resolution mechanisms, in case a party breaches the agreement. You should anticipate how you would enforce your intellectual property rights under the agreement and identify intellectual property offices you may contact where there is a violation of your IP rights. Preferably, you should state your jurisdiction as the applicable governing law and venue for resolution of the agreement, to ensure that disputes that arise from the agreement are resolved within your jurisdiction.
Inquire about the processes of a potential partner
Verify you are working with a firm that follows correct procedures. The correct practices are ultimately what will safeguard your work, rights and information. The questions below provide an excellent starting point.
- What contracts do they have in place with their workers and consultants?
- Is any of their work subcontracted? If so, how do they safeguard their intellectual property?
- Are they utilizing appropriate project management tools?
- Where do they keep their servers and source code? Is there a backup support mechanism in place if something occurs at a local office?
- How does their team interact and exchange documents?
- How do they ensure that data and documents are removed from the possession of departing or dismissed employees?
- Allow employees to utilize personal tools and email, or do they require employees to use just company-authorized resources?
- What is their laptop and internet access security policy?
- Do they have procedures in place for remote employees?
Limit server and data access
Limiting server and data access is also another means of ensuring protection of your intellectual property when outsourcing to third parties. You should ensure that data is stored on your servers. At no point should your data reside in any place other than on your cloud. Allow the vendors to work remotely via your cloud services, where you can closely watch everything they do and have documented proof in the security or data breach.
Access to your server, API and data should also be limited to only what is necessary to complete the outsourced task. If the task requires access to all or a core part of your intellectual property, then you may consider executing some of the task in-house or asking the in-house team to integrate the developer’s work product into the software.
Transition protocols should also be discussed before the project commences. There have been cases of vendors’ refusal to transfer the source codes to their clients when disputes arise or the vendor is moving to another firm. To forestall such occurrences, all applications should be built on your firm’s servers right from the start of the project. Source code should also be stored within your firm’s account on BitBucket, Github, or other similar platforms.
Key questions to ask outsourcing vendor
How do you protect the confidentiality of information?
Before you get down to discuss your ideas, a trustworthy contractor will offer to sign a Non-Confidentiality Agreement (or Non-Disclosure Agreement). Take note of the agreement's period, the precise categories of information that are covered and excluded from it, and if the parties subject to the agreement are properly stated and represented.
How will my data be protected?
Determine if the software developer has the means and capacity to safeguard your intellectual property from unauthorized use, loss, or theft; at the very least, guarantee secure connections, two-factor authentication, a robust password policy and password updates policy, a well-f VPN tunnel, firewalls, and disc encryption. Do they safeguard home routers for remote work as well? What antivirus do they use, and how frequently do they check for system updates?
How will you ensure effective IP rights transfer?
Enquire about how the software development firm treats your collaboration and the ownership of the software product that results. This will help you avoid being forced to deal with a company that wants to create its own products at your expense.
Conclusion
While trying to save time, be more flexible, save money, and increase productivity through outsourcing, it is important to consider the risks to your intellectual property and take the steps necessary to protect your intellectual property. With the knowledge of the importance of the legal framework applicable to your IP, for example, you may review past outsourcing agreements and renegotiate where necessary. You may also limit server and data access to vendors. You will also strategically approach future outsourcing agreements or arrangements by asking the outsourcing vendor key questions.





![15 Software Vendor Interview Questions [Procurement Guide]](/uploads/blog/software-vendor-interview-questions/software-vendor-interview-questions.png)
